Colonial Pipeline Still Mostly Offline After Ransomware Attack
Operators of the Colonial Pipeline are struggling to get fuel flowing at normal capacity after a cyberattack forced a shutdown of distribution system, the largest refined products pipeline in the United States.
The Colonial Pipeline Company was the victim of a ransomware attack that triggered the company to halt all pipeline operations on Friday.
The company said Sunday evening that it was developing a system restart plan, but that some smaller lateral lines between terminals and delivery points are now operational.
Colonial’s mainlines (Lines 1, 2, 3 and 4) remain offline as of Sunday night.
“We are in the process of restoring service to other laterals and will bring our full system back online only when we believe it is safe to do so, and in full compliance with the approval of all federal regulations,” the company said in a statement.
“At this time, our primary focus continues to be the safe and efficient restoration of service to our pipeline system, while minimizing disruption to our customers and all those who rely on Colonial Pipeline. We appreciate the patience and outpouring of support we have received from others throughout the industry.”
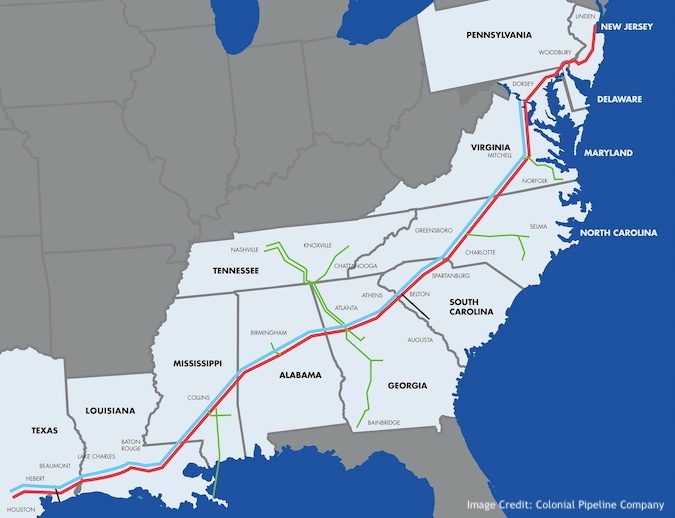
The Colonial Pipeline is the largest refined products pipeline in the United States, transporting more than 100 million gallons of fuel daily through a pipeline system that spans more than 5,500 miles between Houston, Texas and Linden, New Jersey.
The pipeline operator is reportedly working with FireEye on the incident response and investigation.
“The initial information available from Colonial Pipeline and the press coverage seems to indicate that they had the processes in place to detect and contain this type of attacks – before it had an opportunity to be exploited further and cause more damage,” Edgard Capdevielle, CEO of Nozomi Networks, told SecurityWeek. “ I’m sure there will be a financial impact for having to take systems offline in this containment, but imagine an attack where they didn’t have the systems and processes in place and they lost control of their business for an extended period of time. It would make the cost of proactively taking things offline look like a rounding error.”
Not without warning
The incident comes just days after the U.S. National Security Agency (NSA) released a cybersecurity advisory focusing on the security of OT systems, particularly in terms of connectivity to IT systems.
Last year, the NSA and the Cybersecurity and Infrastructure Security Agency (CISA) issued a joint alert urging critical infrastructure operators to take immediate measures to reduce the exposure of OT systems to cyberattacks.
In 2019, an audit from the Government Accountability Office (GAO) showed that the U.S. Department of Homeland Security’s (DHS) Transportation Security Administration (TSA) needed to address weaknesses in the management of key aspects of its pipeline security program.
Following a review in how the TSA manages its pipeline security program, the GAO made a series of recommendations in December 2018 to address discovered weaknesses, which include updating pipeline security guidelines, planning for workforce needs, assessing pipeline risks, and monitoring program performance.
The Department of Homeland Security (DHS) also warned back in 2012 that malicious actors had been targeting the natural gas industry.
Add Comment
You must be logged in to post a comment.



